Code Signing allows app publishers and software developers to ensure security. It provides the integrity of the software, firmware, and code scripts through encryption.
App developers can digitally sign applications using the code-signing process. This acts as a sign of trust and authenticity for users. It is a sign of security that assures users that the app's code is intact and that they can install it on their devices without risk.
However, how does Code Signing secure an app?
This article will help you understand code signing. How does it work with the best practices for implementation ?
What is a Code Signing?
Code Signing is the process of digitally signing a software file. This digital signature helps users validate the publisher or developer of the software. It also allows users to ensure that the software code is intact and its integrity is not compromised.!
This indicates to the users that the software is safe and can be trusted for download and installation on their devices. It also indicates that software can protect the code against malicious cyberattacks. You can use code signing to sign both external and internal software digitally. Further, you can also code sign important security patches, updates, firmware, messages, scripts, containers, and images.
Now that you know what code signing is, it’s time to understand how it works.
How does Code Signing work?
Knowing the hash is crucial to understanding how Code Signing works. Hash algorithms are also vital to checking the integrity of the code when a user installs the software.
A hash function is a mathematical function that takes variable length inputs and returns an output of a defined length. It is an almost impossible mathematical problem to solve. If it is easy to solve cryptographically, it is weak.
Signing the Code
Verifying the Code
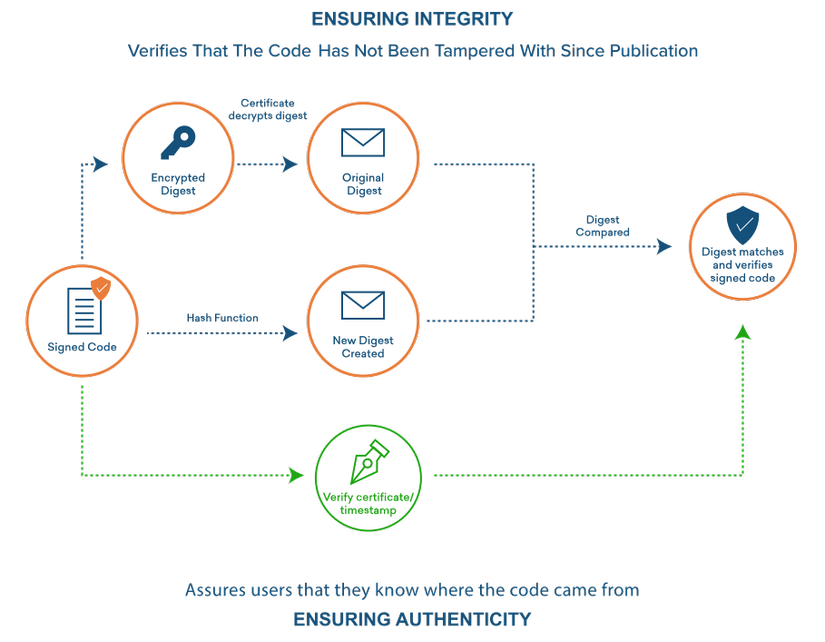
Image Source : [SSL2BUY]
Step 1 CSR Generation and Hashing
The process begins by buying a Code Signing certificate. The application publisher creates a certificate signing request (CSR) containing the necessary details. The data in the CSR is passed through a hashing algorithm.
Step 2 Code Signing Process
The hashed file is signed using the private key stored in a high-security module (HSM). This crypto module needs to be FIPS 140-2 compliant. At the same time, a public key pair and information on the signing authority are fetched from a Code Signing certificate. This information is further digitally signed.
Step 3 Code Bundle
Certificate Authority and public key are stored as a digital signature bundled with the original code file. In addition, you need to add a Code Signing certificate to the bundle. The bundle is now ready for distribution among users.
Step 4 Hash Authentication
A digitally signed hash is bundled with the public key. Therefore, when a user tries to install the software, the system will use the public key to verify the digital signature, which contains a hashed code file.
Implementing Code Signing efficiently is crucial to ensure the security of your software. Therefore, here are some best practices to follow.
Best Practices for Code Signing Implementation
Cyber threats are increasing, and software publishers must safeguard their code scripts. Especially with 93% of organizations suffering from two or more data breaches in 2023, securing your code becomes vital. Therefore, you must ensure efficient Code Signing implementation for better data security.
1. Secure the Private Key
A significant issue with most Code Signing processes is private critical security. Cyber attackers can access it and inject malicious malware if it is not stored securely. The best way to secure a private key is by storing it in an HSM. Based on the CA/Browser (CA/B) Forum requirements to secure private keys, the storage device needs to be FIPS 140-2 compliant.
2. Data Access Policies
Access to critical data and files within your organization needs specific policies. Admin controls to digitally sign files and security keys need restrictive access. You can implement role-based access control (RBAC) policies where a particular person in your organization has permission to access code scripts.
3. Implement the Latest Cryptographic Standards
Ensuring your Code Signing process involves all the latest cryptographic standards is crucial. It ensures that your code scripts are secure against the latest cyber threats. For example, the CA/B Forum requirements now mandate CAs to support a minimum of RSA-3072 encryptions for Code Signing. Similarly, you must follow many other cryptographic standards.
4. Timestamping
This is a best practice that boosts authenticity and trust among customers. Time stamping adds the date and time of the code signing in a digital signature. Therefore, even if your Code Signing certificate has expired, the time stamp lets users know when it was initially signed.
Signing Off
The code signing process is crucial to ensuring the authenticity and integrity of your software. It allows developers to secure code scripts and improve trust among users. Implementing a code signing process for your software with best practices ensures better protection.
However, the most important aspect is executing the code signing process properly, choosing a valid certificate authority, and time stamping the digital signature. So, make sure you get code signing process right for increased user trust and a sense of authority.